Configuration Environment
June 29, 2024 at 4:56 AMOn the Environment configuration page you have to enter the required information of your Active Directory environment.

Active Directory Environment
Domain controllers
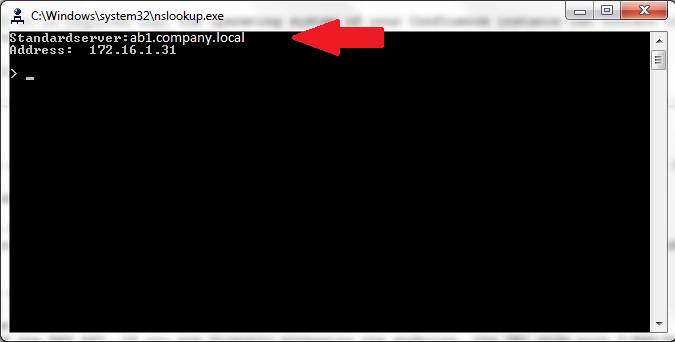
The domain controller represents the Active Directory server(s) used to authenticate and authorize your users. You can find your currently used domain controller when executing
nslookup
on your Windows client.
Multiple domain controllers can be defined by putting a single IP or DNS name in every input field.
- Each IP must serve the same Active Directory domain.
- Please note that the first domain controller is used by default. All other DCs are only used if ADI failed to connect or failed to authenticate the user to the previous one.
- There is no real Round Robin implemented. All additional domain controllers are used as fallback only.
Port
This option defines the port which is used by Active Directory. By default the port is set to 389. The port is used for every defined domain controller.
Please note, that Microsoft provides access to Active Directory through TCP and UDP over port 389. TCP-only is used for port 636, 3268 and 3269, see Active Directory and Active Directory Domain Services Port Requirements.
Use encryption
Choose between:
| Option | Value |
|---|---|
| STARTTLS | Active Directory provides STARTTLS over TCP/UDP port on 389 (default) and TCP-only on 3268. Port 3268 is used by the Global Catalog. |
| Lightweight Directory Access Protocol over SSL (LDAPS) | Active Directory provides LDAPS TCP over port 636 (default) and 3269. Port 3269 is used by the Global Catalog. LDAPS is deprecated and should no longer be used. |
| None | Disabled |
If you want to use LDAPS the Port option has to be manually set to 636 or any other port your domain controller uses.
Hints
- Active Directory uses StartTLS on port 389/3268 for encrypting the communication after the connection has been established.
- LDAPS listens on port 636/3269 and can not be used with STARTTLS.
- All of your domain controllers must provide the same encryption methods. There can not be a primary DC which requires LDAPS and a second DC without having LDAPS enabled.
- If you are receiving the error
AD: Strong(er) authentication required] [AD error code: 8, you have to use STARTTLS instead of None.
Allow self-signed certificates
Instead of installing the Active Directory’s x.509 certificate for LDAPS or STARTTLS connections, this option allows NADI to accept any self-signed certificate.
LDAP network timeout
The LDAP Network Timeout sets the time in seconds after which a connection attempt to the Active Directory is canceled. If the timeout has been reached NADI falls back to local WordPress authentication methods.
The default value for this option is 5 (seconds) which should be more than enough in most cases.
Base DN
The Base DN is the search root when looking up users and role mappings. The value of this option depends upon your Active Directory domain setting and could have a value like OU=users,OU=my organization,DC=domain,DC=tld. If you use a wrong base DN, the users can be authorized but their data can not be fetched from Active Directory. The debug.log contains a warning like:
Attributes for '$user@$upnSuffix': could not be loaded. Does the sAMAccountName or userPrincipalName exist? Is the provided base DN valid?
To fix this error you should try each hierarchical path of the DN:
- OU=users,OU=my organization,DC=domain,DC=tld
- OU=my organization,DC=domain,DC=tld
- DC=domain,DC=tld
As noted in the Security considerations sections this setting should restrict the access as far as possible. At its best please use only the organization unit (OU) where your users and groups are in.
You can find your Active Dirctory Base DN if you follow this step by step guide correctly
- Connect to your Active Directory server with help of Remote Desktop.
- Open Start -> Administrative Tools -> Active Directory Users and Computers
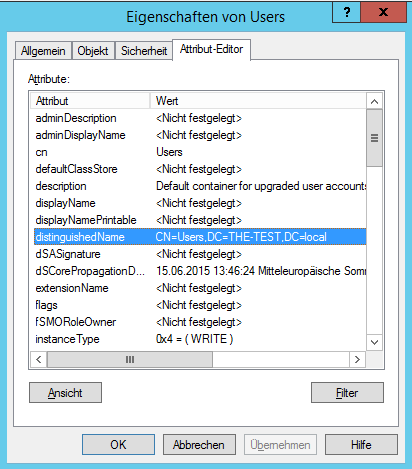
- Right-click on your Domain Controller -> View -> Advanced Features
- Double-click on your Domain Controller -> double-click Users -> right-click Users -> Properties
-
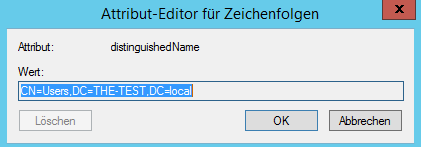
Attribute Editor -> Select distinguishedName in the list -> press View
- Copy your Base DN.
Verify credentials
The username and password are needed to authenticate a member of the target domain in order to connect it to a WordPress site / NADI profile. This is required to assure that you are able to synchronize users of multiple Active Directory domains. Connecting your WordPress site or profile to a domain is required before you can save any configuration.
Domain SID
This options indicates that your WordPress site or NADI profile is currently connected to an Active Directory domain. It will display the domain SID, enabling you to check which Active Directory domain the WordPress site or profile is currently connected to.
NetBIOS name
since 2.0.11 The NetBIOS name is retrieved from the Active Directory configuration and is used during SSO with NTLM. You can not configure this option.
since 2.3.2 Resolving the correct NetBIOS name in an Active Directory forest environment is tricky. NADI iterates over the available domain partition configurations from the most specific DN (based upon the defined base DN) to the most generic DN to find the correct NetBIOS name. If you have issues with resolving the correct NetBIOS name, take a lookt at #153.
Additional domain SIDs
since 2.2.0 Premium Extension: Active Directory Forest
If you are inside an Active Directory domain forest with multiple domains connected, you have to specify each of the domain SIDs in addition to your already connected domain/Global Catalog.
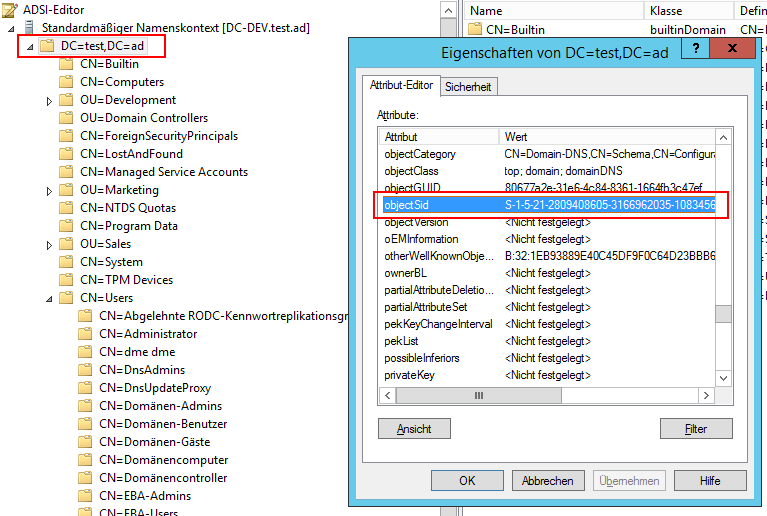
How to find your domain’s SID
- In ADSI Edit connect to the Default Naming Context of each of your domains.
- Right click on the top-level object, e.g.
DC=test,DC=ADand select Properties - Navigate down to objectSID