Configuration Sync to AD
June 29, 2024 at 4:56 AMTo keep everything updated with the current user’s data you can enable a synchronization from WordPress back to your Active Directory.
NADI supports two options how the attributes are synchronized back to the Active Directory:
- Each time a WordPress user changes his profile, the user has to enter his AD credentials. This method has the advantage that no credentials are stored. The trade-off is that it can be annoying for the user to enter his credentials every time he changes his profile.
- Each time a WordPress profile gets updated, a dedicated service account (SA) is used. The SA’s credentials are stored encrypted inside WordPress’ database, which can led to heavy issues if you have a security breach. From a user’s perspective this is the more elegant way as they don’t need to enter their credentials.
Active Directory permissions
In any case, you have to set the correct Active Directory permissions so that LDAP attributes can be stored after the user’s profile has changed. If you did not do it, you will see the following error in your logs/debug.log file:
adLDAP last error: Insufficient access
Setting the permissions without a service account
| Step | Example |
|---|---|
| Use ADSI Edit to connect to your Active Directory | |
| Navigate to the Organizational Unit where your users reside and select Properties from the context menu | |
| On the tab Security choose the name SELF (SELBST) and enable the permission Write |  |
| Click on the button Advanced, navigate to the access permission Write for the principal SELF and click on Edit | 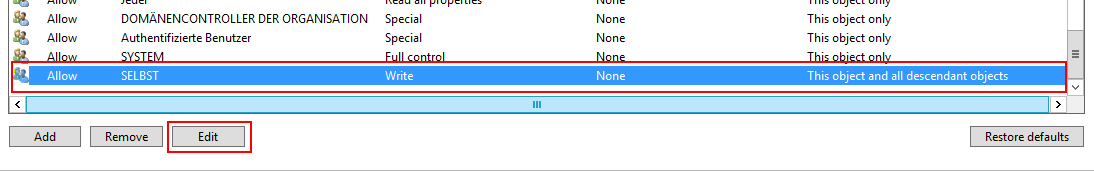 |
| Select This object and all descendant objects from the Applies to select list | 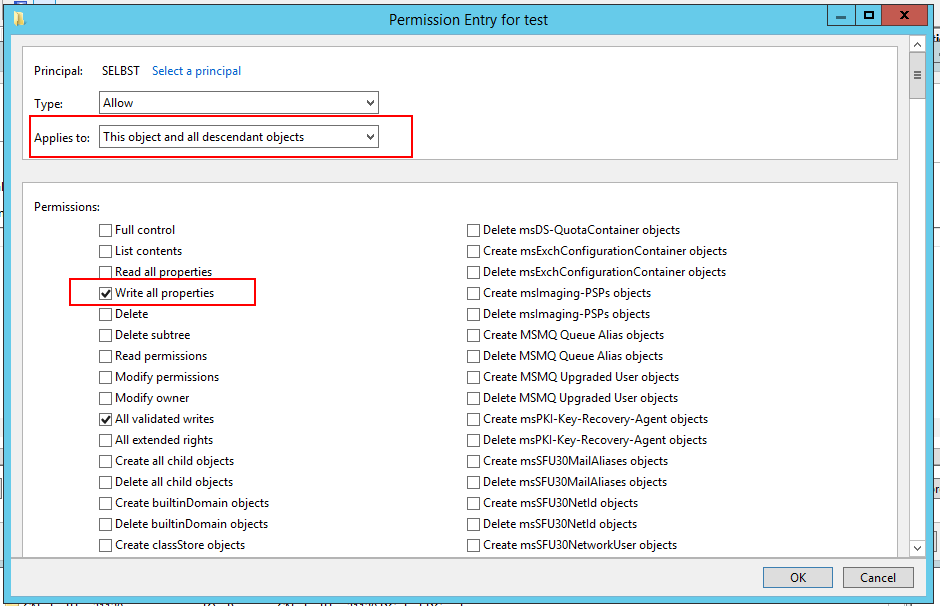 |
| Save the settings |
Setting the permission with a service account
Follow the steps above, but instead of using SELF, assign the permissions to your proper service account.
Error “Insufficient access” still occurs
If, after you have applied the correct Active Directory permissions above, you still receive the error Insufficient access, it might be due to way how the user has been created. If the user has been created created in a previous OU where the permission had not been set, and you moved it to your OU with the applied permissions, the user will keep permissions from the old OU. So, the best solution is to force to reload the permissions of the user with this command:
DSACLS "CN=user,OU=my_ouDC=domain,DC=tld" /P:N
You can use the following PowerShell script to apply the changes to all users of an OU:
# SCRIPT TO FORCE USER OBJECT TO GET INHERITED PERMISSIONS FROM PARENT OU
$ou = "OU=users,DC=domain,DC=tld"
$userlist = Get-ADUser -SearchBase "$ou" -Filter *
ForEach($user in $userlist)
{
$dn = (Get-ADUser $user -Properties DistinguishedName).DistinguishedName
$cn = (Get-ADUser $user -Properties Name).Name
echo "Settings default inherited permissions from parent OU on user $cn"
echo "SETTINGS PERMISSIONS FOR USER $cn" >> dsaclslogs.txt
DSACLS "$dn" /P:N >> dsaclslogs.txt
}
echo "Done. Please consult dsaclslogs.txt if necessary."
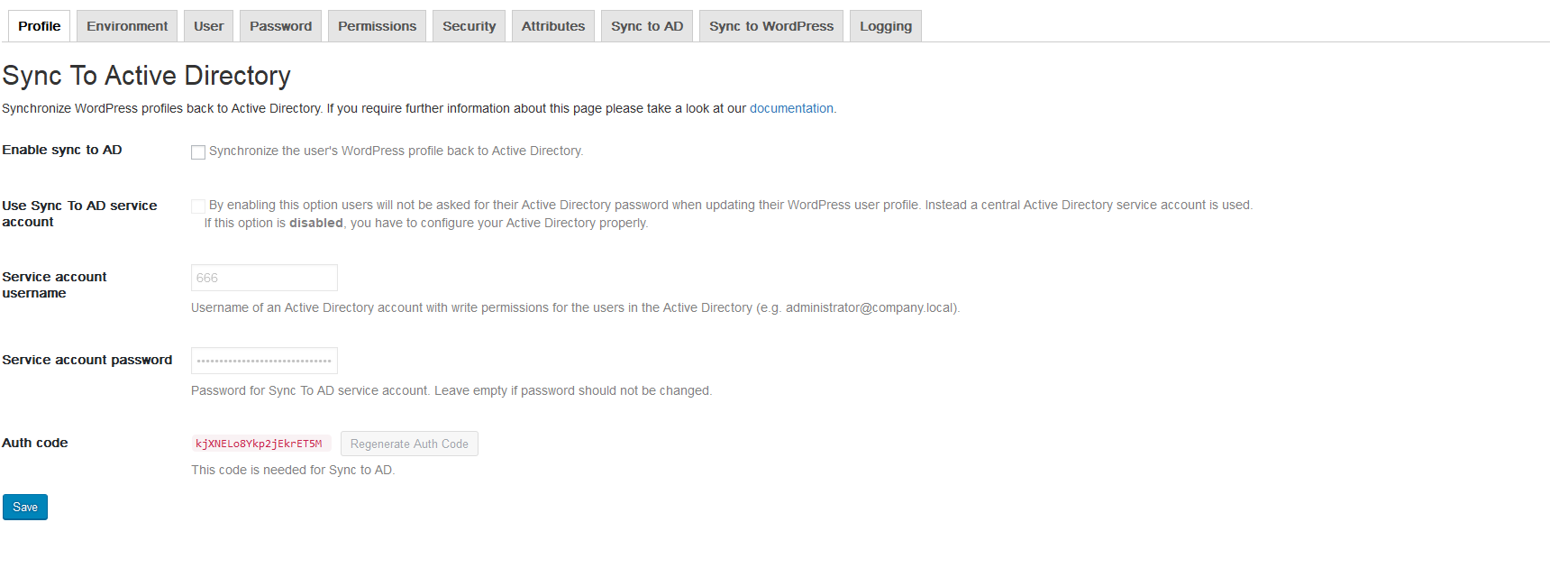
Sync to Active Directory
Enable sync to AD
By enabling this option NADI will automatically synchronize the user’s profile back to the Active Directory when it has changed.
The synchronization is automatically triggered whenever a user profile gets updated through the user’s profile page.
Use Sync To AD service account
By enabling this option users will not be asked for their Active Directory password when updating their WordPress user profile. Instead a dedicated Active Directory service account is used. Please see the notes above.
Service account username
If Use Sync To AD service account is enabled the username of the service account must be defined. Please note that you have to explicitly add the domain information by appending the domain suffix.
Service account password
This option defines a NEW password for the Sync to AD service account. Leave this field blank if you don´t want to change the password.
Auth code
The authentication code must be used if you want to trigger the synchronization with help of a cron job. The menu option Sync to AD shows you the code snippets for wget and curl.