Networking Single Sign On Configure browsers to use Kerberos
June 29, 2024 at 4:56 AMUsing Kerberos implies that your client’s browser must be configured properly!
Depending upon which browser your clients use, you have to set up the Kerberos configuration in a different way. Please note that without a proper configured browser, the Kerberos token is not sent to the server and so SSO will not work!
Internet Explorer
The URL http://webserver.test.ad must be added to Internet options > Security > Local intranet. You can deploy this setting by using a group policy for the node Computer Configuration/Policies/Administrative Templates/Windows Components/Internet Explorer/Internet Control Panel/Security Page/Site to Zone Assignment List. Each of your SSO-enabled sites has to be in the Intranet zone (value = 1).
You can use wildcards like https://*.test.ad.
After you have configured the setting, it should look like this:
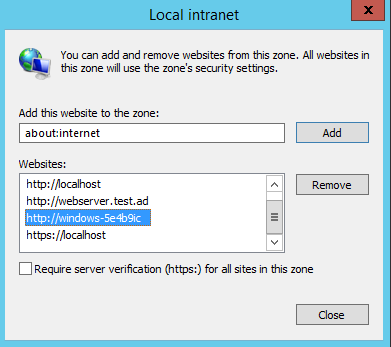
Please note, that enforcing a GPO for Site to Zone Assignment List does no longer allow your users to edit the setting on their own! There are two options:
- Collect each custom configuration and assemble the complete list. In most cases you can use a wildcard on your internal domain like
https://*.test.adandhttp://*.test.adto include all internal sites. - Configure a custom assignment list by using a logon script or something like OpsCode Chef or Microsoft’s Desired State Configuration.
The first option should be the way to go.
Check the other security settings
Please make sure that there your SSO-enabled domain is only entered in the Local intranet zone and nowhere else! If you have falsely entered the same domain in Trusted sites and Local intranet, the first one is used an no Kerberos token is sent by Internet Explorer to the webserver.
Chrome
Newer versions of Chrome do automatically detect the Kerberos negotiation and transmit your token. In case you are using an outdated version of Chrome we highly suggest to update it for security reasons.
If an update is not possible at all, Chrome must be started with the parameter
--auth-server-whitelist="*.test.ad"
like
C:\Program Files (x86)\Google\Chrome\Application\chrome.exe --auth-server-whitelist="*.test.ad
This setting can be automatically deployed by using group policies.
- Download the official group policies for Chrome
- Follow the installation procedure and open the
chrome.admx - Configure a policy for the option
AuthServerWhitelist - Deploy the policy
Firefox
In Firefox you have to go to the about:config page and set the parameters
network.negotiate-auth.trusted-uris
network.automatic-ntlm-auth.trusted-uris
to http://webserver.test.ad.
The deployment of those settings can be done by using the official group policy templates for Firefox, provided by Mozilla.